1Password

Passwords are the most common type of sensitive information that any company owns. It’s also a piece of information that, if leaked or hacked, can lead to catastrophic results for the company and its clients.
To prevent an apocalyptic scenario caused by the leakage of authentication credentials, the team uses 1Password.
Meet 1Password
- 1Password is a Password Manager that provides space for keeping the team’s secrets and sharing them among teammates with a fine-grained level of permissions.
- It provides more tooling integrations that help to save time from memorizing the passwords, secret files or switching over to the vault to lookup and then perform a copy/paste action.
- It also provides the
Watchtowerfeature that notifies the team when it finds weaknesses from their passwords. The reasons could be:- Reusing the same passwords in multiple places.
- Passwords are not complex enough.
- Passwords have been compromised somewhere else.
The 1Password workspace
- Everyone at Nimble gets an invitation to join the workspace on the first day or they can request to join the 1Password team here https://nimble.link/security/. Only @nimblehq.co emails will be able to join.
- For 3rd parties that need access to the vaults, there are up to 5 guests. Guest access is restricted to a single vault.
- Sign in after joining here https://nimble.1password.com.
- After joining the Nimble workspace, all members can access the General vault, which is called ‘Nimble - General’.
-
A Private vault will be created for teammates personal use as well. It means nobody can have access to it besides themself (not even administrators or owners).
Install 1Password
- In addition to accessing directly from the website, 1Password also provides helpful apps for the needs:
- 1Password Chrome Extension, Firefox Add-ons, Safari
- 1Password for Android
- 1Password for iOS
- 1Password for Desktop
- and more. Check out 👉 HERE
-
A suggestion is to have at least the browser extension from section #1 depending on the default/preferred browser of choice.
- Read a secret pair of username and password is very straightforward with the simple GUI provided: either from the website or any other apps: navigate to a specific vault that has access to view, retrieve the specific key for the inquiry purpose.
-
Write a secret item is also simple:
- Pick the vault.
- Choose the appropriate Template (For now, the
Login Templateis the most commonly used and available option. More templates will be mentioned later). - Enter the username/password, and the website the secret should be applied to for the auto-filling helper to work.
-
Delete action is limited to only the vault’s group of administrators. Only the members with admin role can:
- Move an Item to Trash (remove items temporarily; it can still be recovered).
- Empty the Trash (remove items permanently), or
- Delete a vault - this action requires a higher permission.
Using 1Password
Skip this if you are already familiar with the Password manager tools. If this is the first time you heard about it, please keep reading.
The basic usage:
-
In the web browser, after installing the Extension, users will be redirected to a Sign-in screen

-
Click
Sign Inand pick the Nimble workspace. Enter the Master Password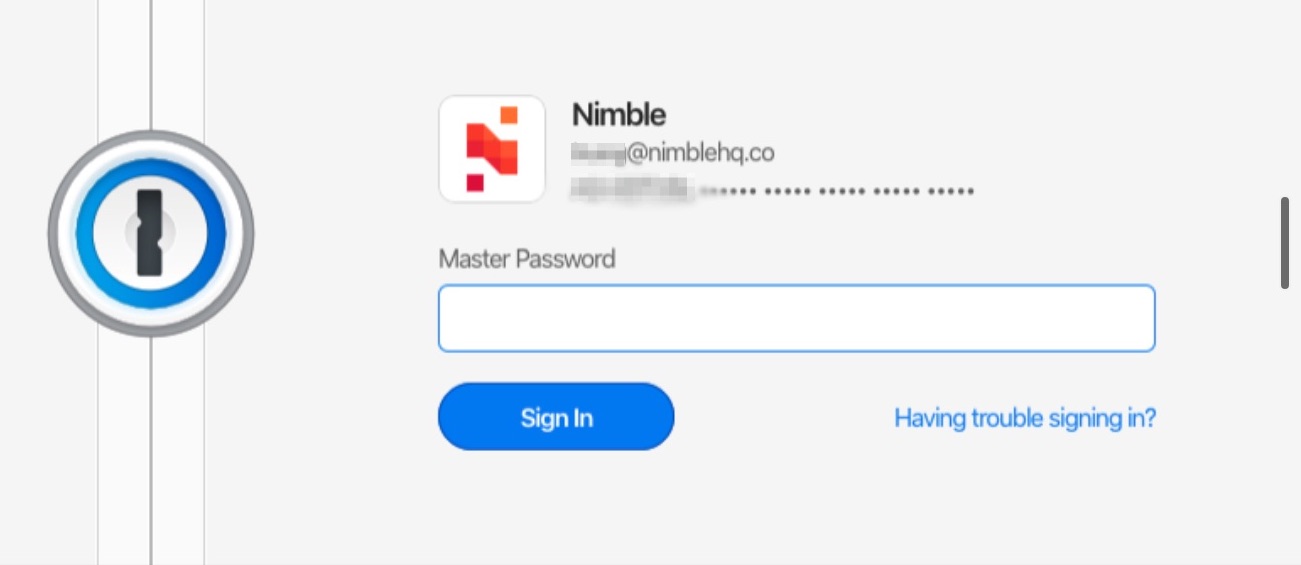
-
There is an icon like this on the toolbar (without the lock 🔒 after signing in)

-
Now, when navigating to a website that requires a Login, say for example: https://teamtreehouse.com/signin - a pop-up will show up to suggest a matching login credential stored in one of the vaults that has access to.
-
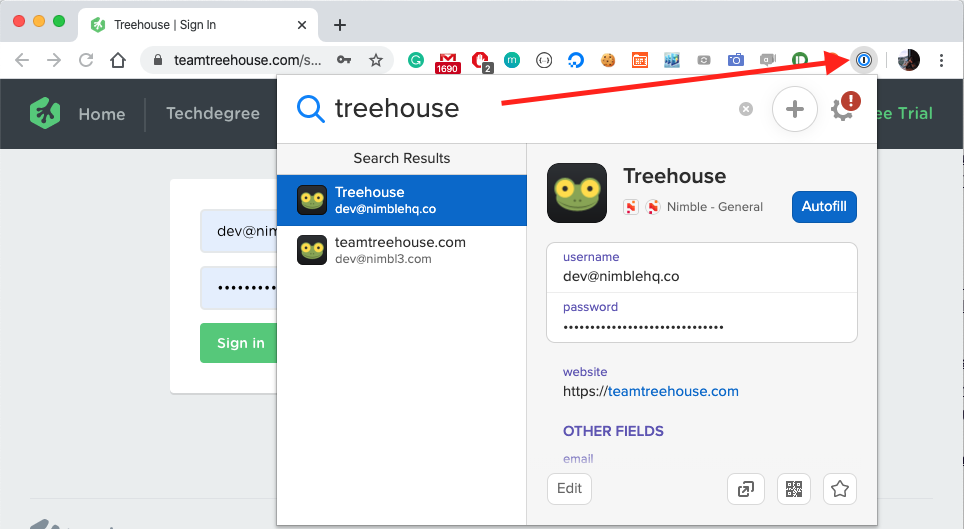
If it doesn’t appear, try to search from the option on the toolbar
-
On mobile, users can also receive the same support after installing the 1Password app. When needing to enter credentials, 1Password will suggest to fill-in the fields

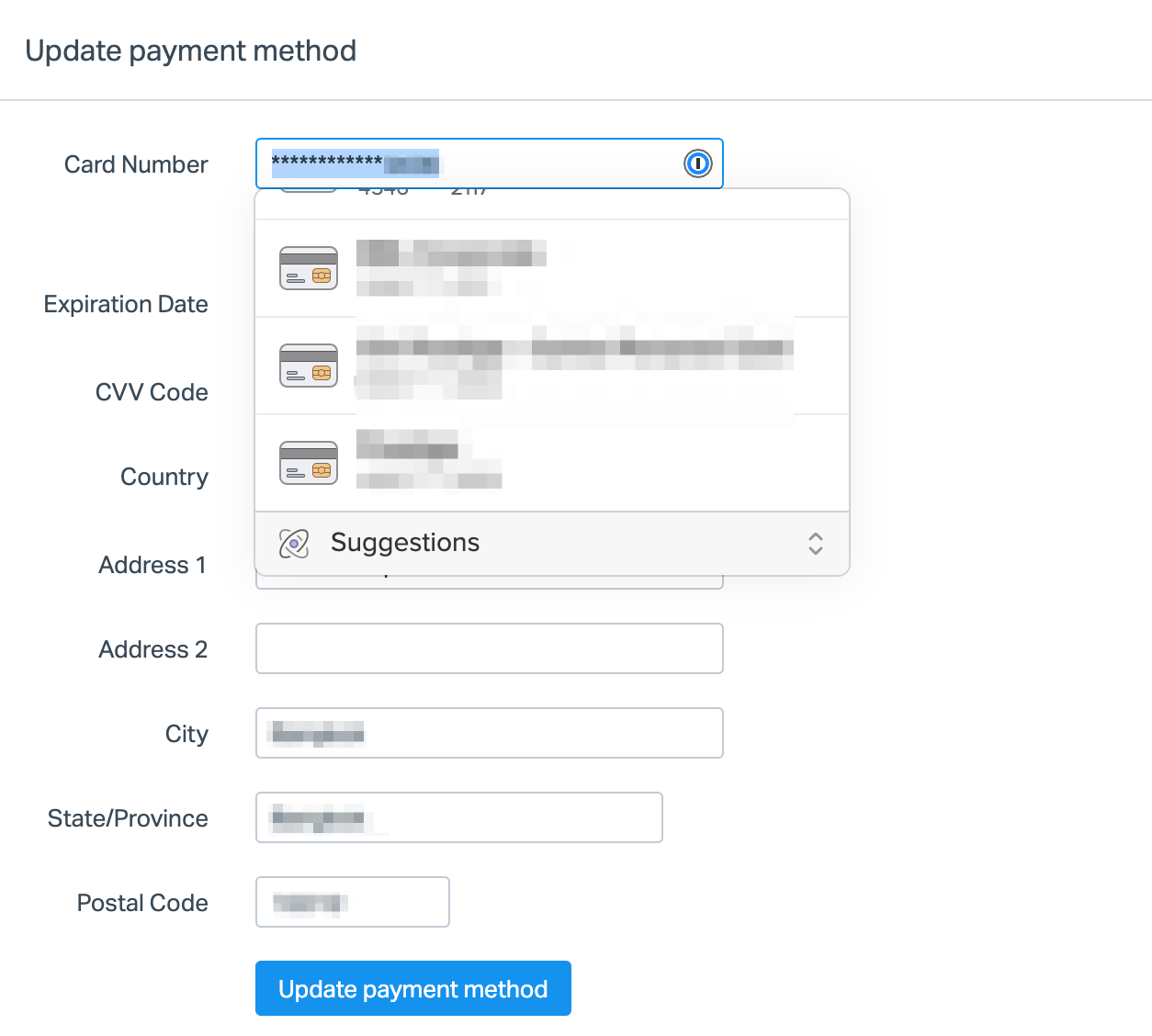
Credit Cards:
The Operations Teams will have the company credit cards in their vault assigned to make it easier while making online payments. Make sure to select the right card. Most of the websites are supported, as shown below:
Sharing Secrets
Whenever someone on the team needs to share secrets with another person, it must be done using 1Password.
Internally, it should be done by pointing a colleague to the proper vault (with the right access).
Externally, sharing credentials or sensitive secrets must be done by using 1Password’s built-in sharing feature.
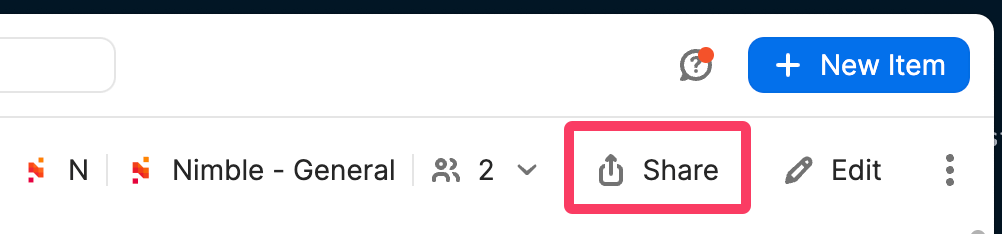
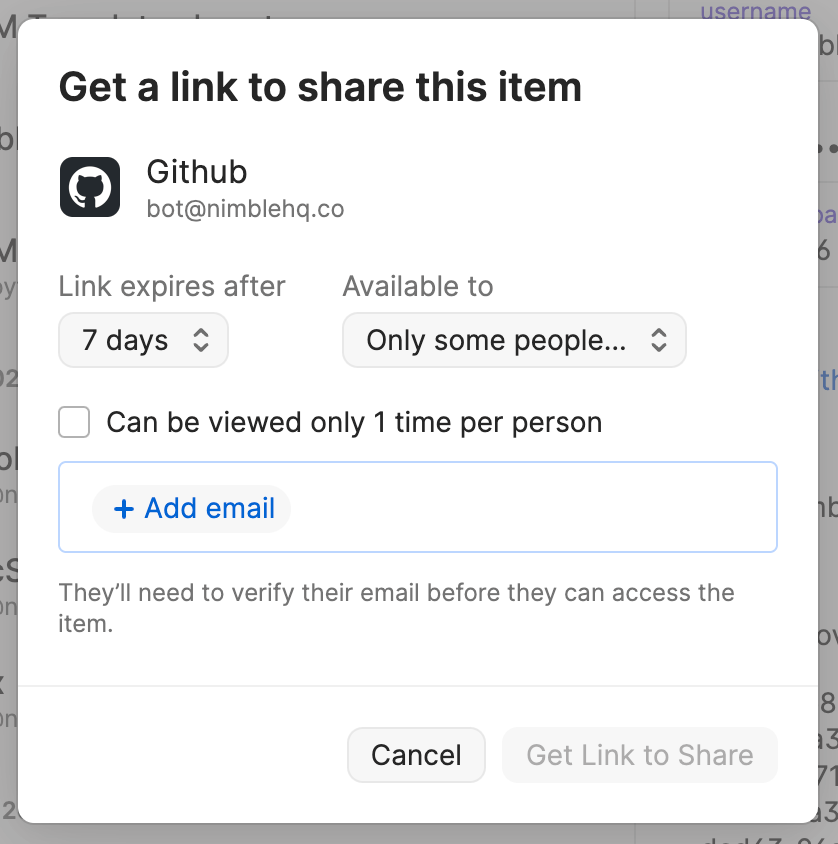
There are a couple of guidelines to follow when sharing a secret externally:
-
Always share with specific people.
Do not use the “Anyone with the link” option because it shares the secret with absolutely anyone with the link, whether they were the intended receipient or not. - Set an expiration time for the share. Do not share a never-expiring secret.
Learn more about 1Password’s item sharing here.
Managing 1Password
This section guides how to add an Item to a vault.
Managing Credentials
-
To add an Item:
- Pick a vault that has access to create an item.
-
Click the Add button and choose the type of item.

- Depending on what kind of data, choose the item type accordingly:
- The basic type is Login.
- For Documentation or SSH Keys, choose Document.
- For API Secret ID and Secret Password, choose an API Secret.
-
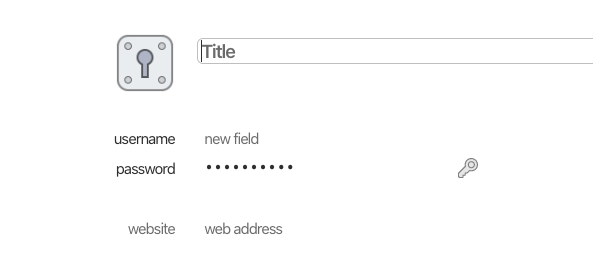
To add a basic username/password pair, choose Login. Then fill in the 4 most important fields:
- Title.
- username.
- password.
- website.
-
To add an SSH Key, keep them as a Document to ensure the integrity. Simply choose Document type, give it a name and drag the key to upload.

- For an API Secret to a platform, choose API Secret and fill in:
- title
- client_id
- client_secret
- url

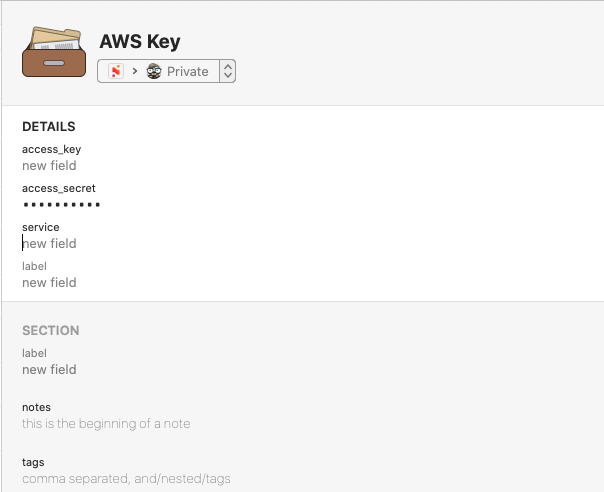
- For AWS service particularly, choose the AWS Key item and fill in:
- access_key
- access_secret
- service
Admin Management
This section guides how to manage content on 1Password as an administrator.
Vault
- The naming convention must follow the pattern
{Organization} - {Location?} - {Domain}. For example:Nimble - GeneralNimble - People OperationsNimble - Thailand - Office OperationsNimble - Vietnam - Office Operations{ClientName} - General{ClientName} - Admin
- Always attach the logo for easier accessibility.
- Apply Access Permission by Group.
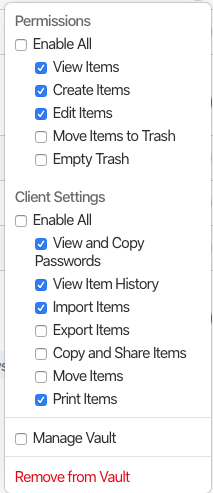
- Permissions:
- Admin permissions: full read/write/delete content, but do not allow to manage the vault.

- General permissions: read/write with some limits like no deletion is allowed.
Group
- A Group is used for grouping members and assigning specific permissions all at once.
-
Naming should follow the 1Password vault’s naming convention. Make it easy to assign people and restrict the permissions accordingly.
E.g., With a vault named
Nimble - Generalthen there must be a group namedNimble - General - Always attach the logo for easier accessibility.
Audit
-
The project admin should check the usage report regularly. This is provided on each vault dashboard via the link
Create Usage Report
-
Admin should recheck if there is any unwanted access to any vault/content.
In case of identifying any suspicious activity, report immediately to the administrator in order to take action.